Network and System Configuration
It is assumed that the instructions for a “New Installation” were followed, “Persistent Storage” and “Security and Sound Files” have been configured.
By default a single /mnt/kd/rc.conf file contains the AstLinux configuration, using options defined as shell script variables. If you do not wish to use the web interface for AstLinux configuration and management, edit the /mnt/kd/rc.conf file as desired and the rest of this document can be ignored.
Most administrators will want to use the web interface, the next step is via the Network Tab in the web interface:
Click “Save Settings” to save any changes, and additionally it creates the /mnt/kd/rc.conf.d/ directory if it did not exist. From that point on the single /mnt/kd/rc.conf file will be ignored, instead all the /mnt/kd/rc.conf.d/*.conf files will be used for the system configuration. All web interface configurations will be saved as /mnt/kd/rc.conf.d/*.conf files.
Every administrator will want to make a few changes in the Network Tab after a “New Installation”, a basic guide is described below.
Network Interfaces
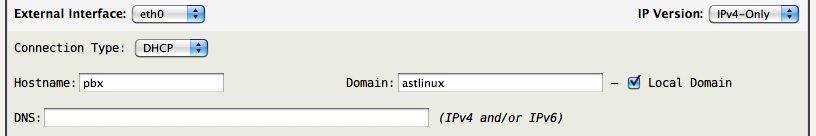
All AstLinux configurations require an external interface to be defined. Select the “Connection Type:” for your situation.
Check “Local Domain” if the “Domain:” is unique to this box. Uncheck “Local Domain” if the “Domain:” is shared via an upstream DNS server.
Tip -> Set “IP Version:” to [IPv4 & IPv6] to enable IPv6 support system wide.
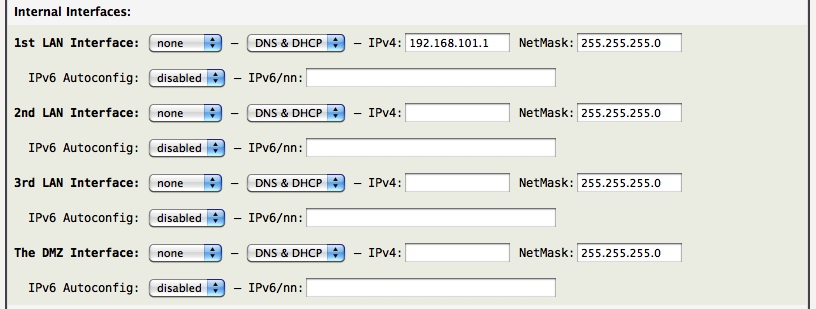
An internal (LAN/DMZ) interface is optional, but is often configured. If AstLinux is used as a router with a public IP address, one or more internal interfaces will need to be defined. Even if AstLinux sits behind the public router using a private IPv4 external address, it is often desired to place IP phones off an internal interface such that the “AstLinux System” (AstLinux hardware, ethernet switch, IP phones, etc.) connects to the pre-existing network with a single network cable.
Tip -> Single interface hardware can utilize VLAN's to create tagged internal interfaces with the help of a managed ethernet switch.

Note -> Interface changes require a Reboot to apply the changes.
Firewall
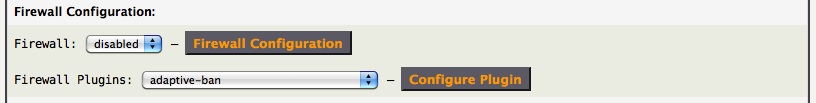
AstLinux provides an IPv4 / IPv6 Stateful Filtering Firewall, based on the excellent Arno's IPTABLES Firewall (AIF) script, developed by Arno van Amersfoort. The Firewall is disabled by default.
A feature of AIF is Firewall plugins that can add specific functionality outside of the core script.
Detailed Info -> Firewall Plugins
The default configuration files are located in /mnt/kd/arno-iptables-firewall. Do not directly edit these files! Either use the web interface or copy variables you wish to set from the firewall.conf file to the Advanced Configuration (/mnt/kd/rc.conf.d/user.conf file). The web interface should handle most use cases and is the recommended method.
Tip -> The Firewall must be enabled for a LAN/DMZ client to access a server upstream via the external interface.
Tip -> VPN's require the Firewall to be enabled, and each have associated firewall plugins that will be automatically enabled.
Note -> If you are currently accessing the web interface via the external interface, be certain to add a “Pass EXT→Local, TCP, 0/0, 443” firewall rule before enabling the Firewall. But in production, keep the number of “Pass EXT→Local” firewall rules to only what is absolutely required when that interface has access to the public internet. Use a VPN to remotely manage your AstLinux system.
Network Time
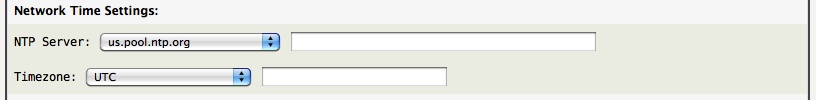
It is important for your AstLinux box to have the proper time set, therefore on every boot the system automatically tries to get the current time from an upstream NTP server. Use the Network Time Settings above to define the NTP server(s) (local or remote) and your local timezone.
Additionally, a local NTP server is automatically enabled to support local network devices and IP phones.
Detailed Info -> NTP Client/Server (chrony) Configuration
SMTP Mail Relay
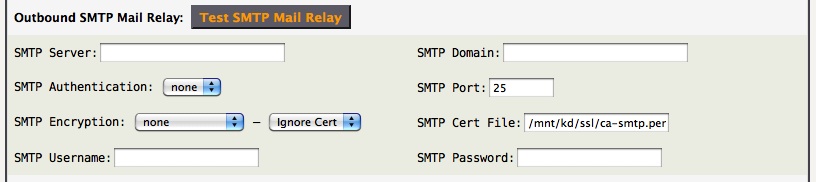
There are many situations when it is desired for AstLinux to send an email, eg. voicemail messages, error notifications, etc. . Define the appropriate credentials for your upstream SMTP server.
Common “SMTP Port:” values are: 25, 465 or 587.
The “SMTP Cert File:” only applies if [Check Cert] is selected.
Tip -> Use the Test SMTP Mail Relay button to test your SMTP settings.
IPv6 Tunnel

If you only have IPv4 connectivity, it is possible to create a tunnel via IPv4 to support IPv6 connectivity. One common service is www.tunnelbroker.net by Hurricane Electric.
Detailed Info -> IPv6 Tunnel Configuration
Dynamic DNS
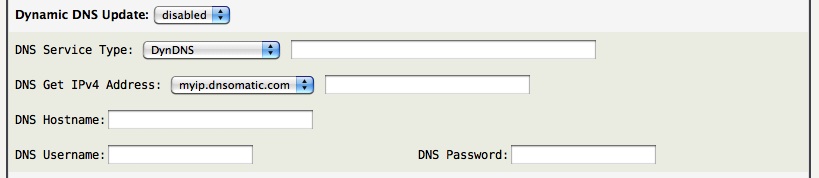
The Dynamic DNS service allows users with (often or seldom) changing public IPv4 addresses to set a public DNS record to consistently reach your AstLinux box on the public internet. A Dynamic DNS provider is required, supplying you with the required credentials.
Available methods: [disabled], [inadyn] or [ddclient]
Tip -> When enabled, it is recommended to use [ddclient] as the method since it is actively supported and supports SSL updates to protect your credentials.
Network Services

Many, many Network Services are supported by AstLinux. Too many to itemize and describe here, but the more featured services have detailed information within this documentation.
Detailed Info -> DNSCrypt Proxy Server
Detailed Info -> XMPP Server Configuration
Detailed Info -> LDAP Server Configuration
Detailed Info -> Zabbix Monitoring Configuration
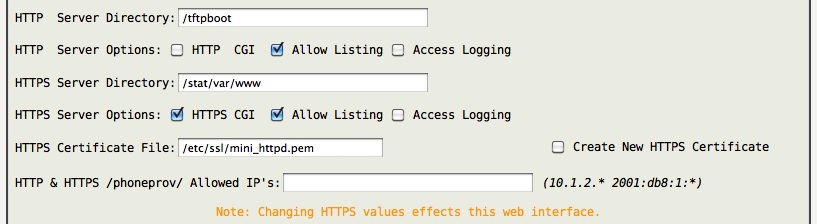
THe HTTP/HTTPS settings control the built-in web server. The web server is used for the web interface as well as serving files for phone provisioning and other situations.
After you have visited the Prefs tab and specified the “Distinguished Name:” section (in the Prefs tab), you may check “Create New HTTPS Certificate” followed by “Save Settings” (in the Network tab) to generate a custom self-signed certificate for the web interface.
Note -> If you manually create the /mnt/kd/phoneprov/ directory, HTTP/HTTPS serves files under the /mnt/kd/phoneprov/ directory with URL paths beginning with /phoneprov/ . Be sure to consider restricting /phoneprov/ access as shown above.
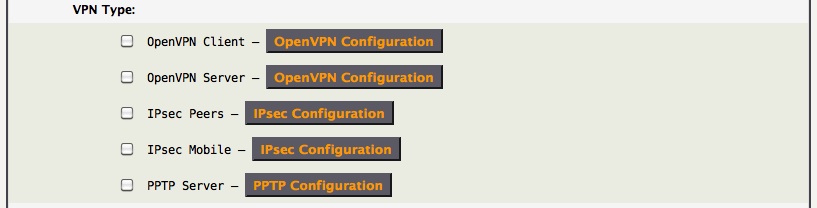
A VPN (Virtual Private Network) Network Service will allow remote users to access the AstLinux box, and/or selected subnets, in a secure manner over an insecure public network, such as the internet.
Tip -> Best practice is to never open HTTPS to the public internet for AstLinux administration, but rather enable a VPN and use HTTPS within the VPN tunnel.
VPN Types and Uses:
- OpenVPN Client - Act as an OpenVPN client connecting to a remote OpenVPN server.
- OpenVPN Server - Act as an OpenVPN server to allow remote OpenVPN client's to access selected network subnets.
- IPsec Peers - Tunnel routed local and remote subnets using static IP addresses.
- IPsec Mobile - Act as an IPsec server to allow remote IPsec client's with dynamic IP addresses to access selected network subnets.
- IPsec strongSwan - Act as an IPsec endpoint using strongSwan.
- PPTP Server - Do not enable this server unless absolutely required for compatibility. Both OpenVPN and IPsec are more secure choices.
Detailed Info -> OpenVPN Configuration
Detailed Info -> IPsec VPN Configuration
Detailed Info -> IPsec VPN (strongSwan) Configuration
Note -> VPN's require the Firewall to be enabled, and each have associated firewall plugins that will be automatically enabled.
UPS Monitoring
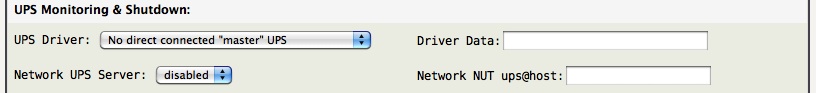
AstLinux uses the Network UPS Tools (NUT) package to monitor Uninterruptible power supplies (UPS) via USB and Network connections.
Detailed Info -> Uninterruptible Power Supply Monitoring
Advanced Configuration

Not every configuration option of AstLinux has a web interface implementation, in those cases the configuration variables must be defined manually. The “User System Variables:” is for such a case, and edits the /mnt/kd/rc.conf.d/user.conf file by clicking on the Edit User Variables button.
Configuration variables are specified using the format:
FOO_OPTION="text data value"
Note -> A space character is not allowed either side of the required = character.
Note -> A # character acts as a comment to the end of the line.