Firewall Overview
AstLinux provides an IPv4 / IPv6 Stateful Filtering Firewall, based on the excellent Arno's IPTABLES Firewall (AIF) script, developed by Arno van Amersfoort.
Default Allowed Traffic Flow
By default, with the firewall enabled and no added firewall rules, the allowed traffic flow is as follows:
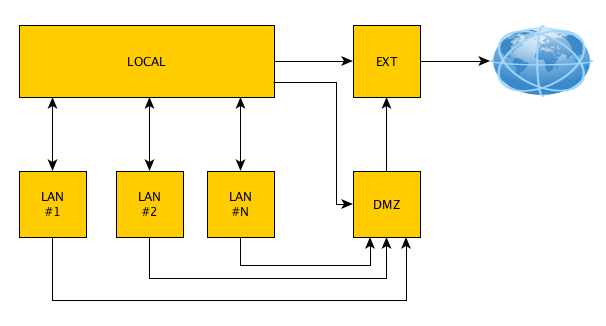
Note -> By default any LAN to LAN traffic is not allowed.
Note -> WireGuard and OpenVPN virtual networks are treated as LANs.
Note -> Using the DMZ requires at least one LAN defined.
DMZ Traffic Flow
In networking the DMZ (DeMilitarized Zone) can have various meaning. In AstLinux, the default DMZ firewall rules are as follows:
- Drop all DMZ→Local traffic
- Drop all DMZ→LAN traffic
- Allow DMZ→EXT (internet)
- Allow LAN→DMZ (includes WireGuard and OpenVPN virtual LANs)
- Allow Local→DMZ
The DMZ makes a great place to place servers and LXC containers, isolated to your network and AstLinux box, but reachable from any LAN and AstLinux itself.
Given the DMZ defaults above, any DHCP, DNS, NTP requests to Local are dropped, so …
Commonly accept these:
Pass DMZ->Local UDP 0/0 53,67,68,123 Pass DMZ->Local TCP 0/0 53
You may also want mDNS (UDP 5353)
To disable DMZ→Local logging, uncheck the following:
Firewall sub-tab:
___ Log Denied DMZ interface packets
If you later need to debug, you can re-enable this setting.
For the Pi-Hole case, the DMZ is perfect. The Pi-Hole can use AstLinux's DNS-over-TLS as it's upstream feed, and dnsmasq's DHCP can be configured to give out the Pi-Hole DMZ address for DNS.
Firewall Plugins
Related Info -> Firewall Plugins
Firewall External Block List
Related Info -> Firewall External Block List