OpenVPN Client Networks
In many cases, the OpenVPN connecting client is only a single IP address gaining remote access via the VPN tunnel.
Though there are situations where the OpenVPN connecting client has local networks defined, which the OpenVPN server endpoint would like to access.
Note -> The additional OpenVPN configuration commands necessary to access client networks is performed only at the OpenVPN server endpoint.
The best way to describe this configuration is by an example:
Example Assumptions
For this example, the Server Network IPv4 NetMask is 10.8.1.0 255.255.255.0
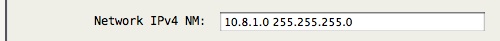
Let us assume the client has a local network of 192.168.222.1/24 that we want the server endpoint to access.
Tip -> While it should not matter in general, if all your clients support a Topology of subnet, it is suggested to specify that.

OpenVPN Server Configuration
The first step is to add the following Raw Commands to the server configuration:
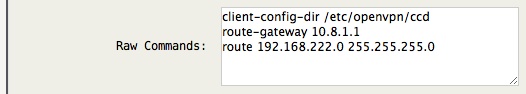
Note -> If you are using Topology “subnet” it is important to specify the route-gateway to the first (.1) address of your server IPv4 network. If you are not using Topology “subnet”, defining route-gateway is not necessary and it will create the route properly by default.
OpenVPN CCD File Configuration
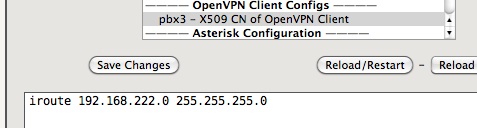
Using the CLI (command line interface) create a file with the same name as the CommonName of your client, in this case “pbx3” in the ccd directory:
/mnt/kd/openvpn/ccd/pbx3
iroute 192.168.222.0 255.255.255.0
add the iroute command for the desired client network(s). Make sure your ccd file has “other” read permissions since OpenVPN runs with “nobody” privileges.
After the ccd file is created, it can later be edited via the Edit tab using the web interface, (AstLinux 1.1.1 and later).
So you might ask, “why do we need both a route and iroute command” ? The route command in the main server configuration adds a system wide route to the routing table, in contrast the ccd iroute command adds an internal route within OpenVPN. Therefore, the route command directs the packet to OpenVPN, and then the iroute command directs the packet to the proper OpenVPN client when connected.
Tip -> The ccd files may be edited without having to restart the OpenVPN server, since every time a client connects matching the CommonName the latest ccd file contents will be used.
Tip -> If a ccd file of DEFAULT exists, all non-matching CommonName clients will use it's file contents, though not required.
Finally, after all the above steps are completed substituting your network values, restart the OpenVPN Server, the proper routes should be in place when the OpenVPN client connects. If you still can't reach the client endpoint's network, read the next section on configuring the firewall at the client endpoint.
Firewall Configuration
By default, both at the OpenVPN client and server endpoints, the firewall prevents packets to the local LAN interfaces of each respective endpoint. This can be changed by accessing the Firewall Configuration sub-tab via the Network tab:
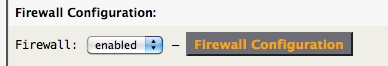
For each endpoint, select which LAN interface that is allowed to have access to the VPN tunnel.

In this example, at the client endpoint, the “1st LAN Interface” has a 192.168.222.1/24 network defined.