Universal Plug'n'Play (NAT-PMP and UPnP)
Universal Plug'n'Play (UPnP) is a technology introduced by Microsoft that allows for easy configuration of port forwarding. Nowadays it is used by many network clients which rely on it to get proper access to the Internet. UPnP is also used by some game consoles, such as the Xbox 360 and the Playstation 3.
NAT Port Mapping Protocol (NAT-PMP) is a technology similar to UPnP that originates from Apple. Unlike UPnP, it is currently an IETF standard, and a number of OS X, iOS, Linux and Windows applications support it. NAT-PMP is basically a simple and sane replacement of UPnP for automating the process of creating port mappings in NAT.
Note: AstLinux 1.0.4 or later is required
Note: AstLinux 1.2.3 or later is required for 'Port Control Protocol' NAT-PMP/PCP support.
Either NAT-PMP or UPnP (or both) may be enabled in AstLinux via the Network tab:
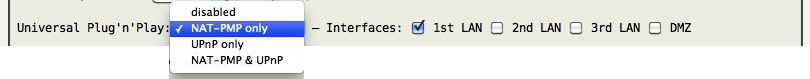
By default both NAT-PMP and UPnP are disabled, and that is the suggested setting for most users.
But, since you are reading this, there are situations where dynamically creating port mappings in NAT is necessary. If so, first try enabling NAT-PMP only and see if your network clients or devices support it.
If it turns out enabling NAT-PMP only does not support your clients, then as last resort enable both NAT-PMP & UPnP so your clients can choose which method of Universal Plug'n'Play is desired.
Note that at least one of the Interfaces: needs to be checked for Universal Plug'n'Play to be enabled.
Any changes to the Universal Plug'n'Play options may be applied by selecting Restart Univ. Plug'n'Play and clicking the Reboot/Restart button.
The Status tab will show a Universal Plug'n'Play (NAT-PMP and UPnP) Leases: section if it is active, and display any active leases.
Security considerations
The topic of Universal Plug'n'Play is not complete without discussing security. Neither NAT-PMP nor UPnP provides any authentication mechanisms, so by default any network application within the selected interface's network may dynamically define NAT EXT→LAN firewall rules. Technically, a worm or malware program could use this function to compromise security.
Within AstLinux there are a few power user features to help minimize the security risks.
- The configuration variable
UPNP_ALLOWdefaults to not being defined, so any client within the selected interface's network may dynamically define NAT EXT→LAN firewall rules. SettingUPNP_ALLOWto an IPv4 address, or space separated list of IPv4 addresses, will restrict only those addresses to be able to define NAT EXT→LAN firewall rules. For example if your XBox is assigned the IPv4 address 192.168.101.90, settingUPNP_ALLOW=“192.168.101.90”will only allow your XBox to define NAT EXT→LAN firewall rules.
- The configuration variable
UPNP_SECURE_MODEdefaults toUPNP_SECURE_MODE=“yes”which limits clients to add mappings to only their IPv4 address. SettingUPNP_SECURE_MODE=“no”will disable “secure mode” but may be required in some situations.
- Users with networking experience may define a separate internal interface LAN or DMZ via a VLAN to contain only Universal Plug'n'Play clients. Then using a managed switch, configure these clients on this special Universal Plug'n'Play network. The Interfaces: setting above would only be this one special network.
- Only port numbers 1024 through 65535 are allowed to be remapped for the external interface and also by default on the internal interface(s). The variable
UPNP_ALLOWmay optionally specify the allowed internal port-range along with the IPv4 address, defaulting to 1024-65535 . For exampleUPNP_ALLOW=“192.168.101.90~3000-4000”will allow an internal port range of 3000-4000 for IPv4 address 192.168.101.90.