OpenVPN Access Policies
Configuring client-specific rules and access policies
Here is a good howto for this:
https://openvpn.net/index.php/open-source/documentation/howto.html#policy
Additionally in AstLinux the following must be done:
- In the Firewall config “Allow OpenVPN Server tunnel to xx LAN Interface” must not be checked!
- The iptables rules should be put into
/mnt/kd/arno-iptables-firewall/custom-rulesfile into theFORWARD_CHAIN. - Because the limited users have still access to the Astlinux server itself, you could either
- create a Firewall rule like
Deny LAN→Local - Proto TCP/UDP - Source 10.8.2.0/24 - Port 0-65535for each of the limited virtual subnets - or create another iptables rule:
iptables -A INT_INPUT_CHAIN -s 10.8.2.0/24 -j DROPfor each subnet
- The easy way is to push the internal LAN route in the OpenVPN server config (push “route 192.168.3.0.255.255.255.0” in this case).
- The more secure way is NOT to push the route in the OpenVPN server config, but instead push only the relevant allowed destinations in the OpenVPN ccd/client file like
push “route 192.168.3.200”, but in this case the “Employees Class” from the example wouldn't work, cause there is no file to include the routing.
Examples
OpenVPN Server Config
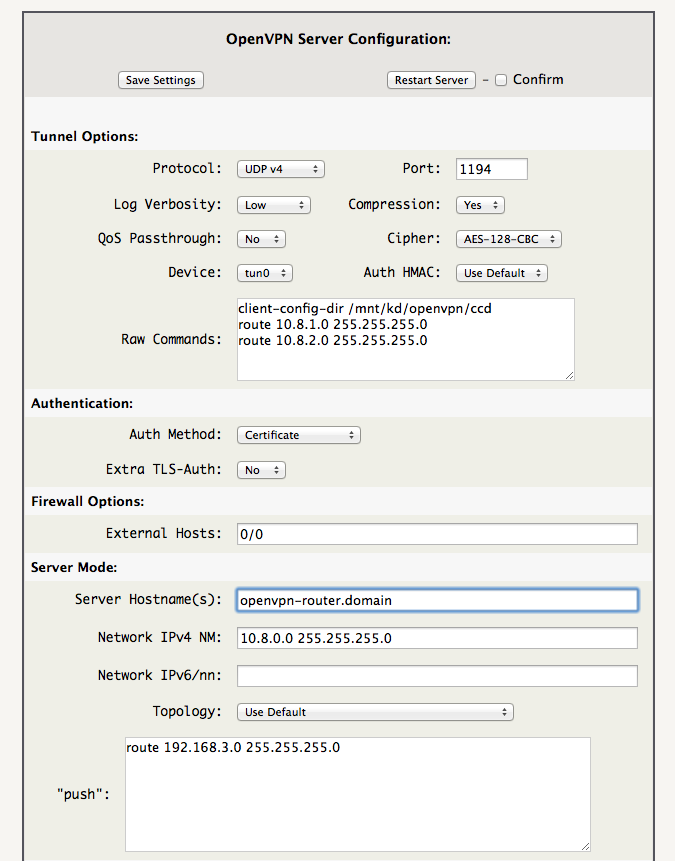
Note: It is very important that Topology “Use Default” is used and NOT “Subnet”!
/mnt/kd/arno-iptables-firewall/custom-rules
# Put any custom (iptables) rules here down below: ################################################## # Employee rule iptables -A FORWARD_CHAIN -i tun0 -s 10.8.0.0/24 -d 192.168.3.100 -j ACCEPT iptables -A INT_INPUT_CHAIN -s 10.8.0.0/24 -j DROP # Sysadmin rule iptables -A FORWARD_CHAIN -i tun0 -s 10.8.1.0/24 -d 192.168.3.0/24 -j ACCEPT # Contractor1 rule iptables -A FORWARD_CHAIN -i tun0 -s 10.8.2.0/24 -d 192.168.3.200 -j ACCEPT iptables -A INT_INPUT_CHAIN -s 10.8.2.0/24 -j DROP
/mnt/kd/openvpn/ccd/sysadmin
ifconfig-push 10.8.1.1 10.8.1.2 ;push "route 192.168.3.0 255.255.255.0"
/mnt/kd/openvpn/ccd/contractor1
ifconfig-push 10.8.2.1 10.8.2.2 ;push route 192.168.3.200
The “push route …” commands are optional (without the “;”)(see above)